
Why do people say you should be careful when connecting your laptop to the WiFi in a cafe or any public area?
Think of a baggage claim at the airport.
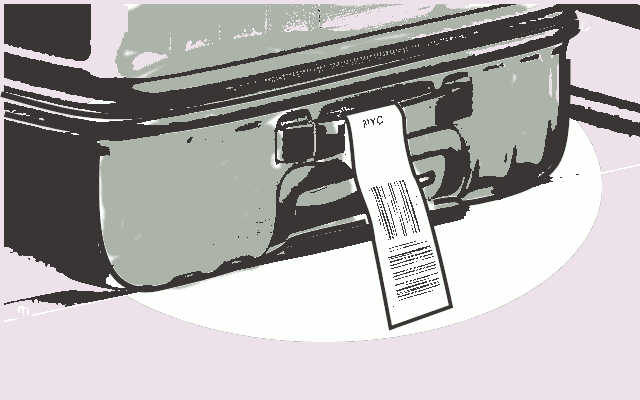
Baggage pickup is based on the honor system. Different bags do look alike. Sometimes people will grab someone else's suitcase that looks like theirs. Hopefully, they will then check the tag and put it back.
WiFi and similar networks work like a baggage claim.
The computer world is full of networks: WiFi, Bluetooth, cellular data networks, old-style wired Ethernet, satellite links, and long trans-oceanic cables.
Computers are omnivorous: with the right software, they will gladly use whatever kind of network you have: USB cords, cable television coaxial cables, land-line telephone wires— these can all be used to send and receive messages.
WiFi usually works as a "shared-access" network. This means that multiple computers can communicate using the same WiFi network.
A central "access point," usually a WiFi router, has a radio receiver and transmitter. Similarly, any computers or devices like your laptop or smartphone, also have radio receivers and transmitters. These radios help these devices exchange messages.
Since the WiFi network is shared by all these devices, they have to somehow identify each other.
Each device on the WiFi network has a uniquely assigned code, a number called its address.
Messages on networks, just like all information exchanged by computers, consist of a sequence of numbers. Each WiFi message is preceded by an address that announces the intended recipient of this message.
In our analogy, if the message itself is a suitcase, then the address is the baggage tag on the suitcase.
But "shared access" means that when you send any WiFi message to another device, every other device in your WiFi network can also see that message.
The space around a WiFi access point is thick with messages, like a conveyor with baggage belonging to many passengers. Normally, your laptop or phone's radio is configured to do the right thing— it looks at the address of each message and ignores it if it's not addressed to it.
But you can configure your radio to act in "promiscuous mode," i.e., to open every message. If you do, you can see all these messages.
To prevent hackers from reading your messages, your computer needs to encrypt the contents— replace all the numbers in the message with different numbers, so that a reader cannot understand the message. But that's a separate topic.
For any shared-access medium like WiFi, you cannot prevent anyone on the network from looking at your messages— a good reason to be cautious at public WiFi hotspots.